- allowlisting specific IP ranges for applications deployed on Porter
- integrating with other AWS tools such as AWS WAFv2
- using AWS ACM certificates
Requirements
- A Porter-managed Kubernetes cluster
- Access to your DNS provider. For this example, we will use CloudFlare, but Route53 is also supported.
- A domain name which can be wildcarded. For this example, we will use
stefan-2.porter.run- Using a wildcard domain is strongly recommended as you can then create multiple applications which are exposed to internet through Porter, without any further changes in future
DNS Validation
Skip this step if you are using Route53, as Porter can perform the validation on your behalf. When your ALB is up and running, you will have to ensure that your new AWS Certificate Manager (ACM) Certificate is validated. AWS does this by creating a CNAME record which must resolve to an automatically generated value.AWS Certificate Manager - CNAME
-
In your AWS console, navigate to the region that your cluster was deployed in. You can find this from your Porter dashboard in the
Infrastructuresection, in the Configuration tab. -
After selecting the correct region, search for
AWS Certificate Managerin the AWS Console search bar. -
Select
List Certificatesfrom the bar on the left. - Find the domain name which matches the domain that you provided to Porter, then click on the Certificate ID.
-
The status for this certificate should be
Pending validation.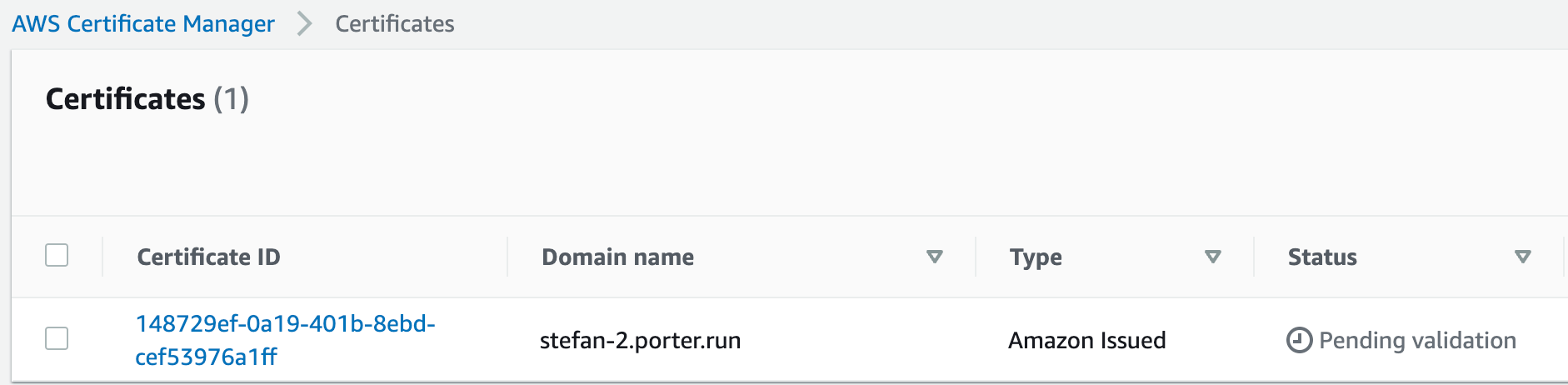
-
Scroll down to
Domains. -
Take note of the
CNAME nameandCNAME value.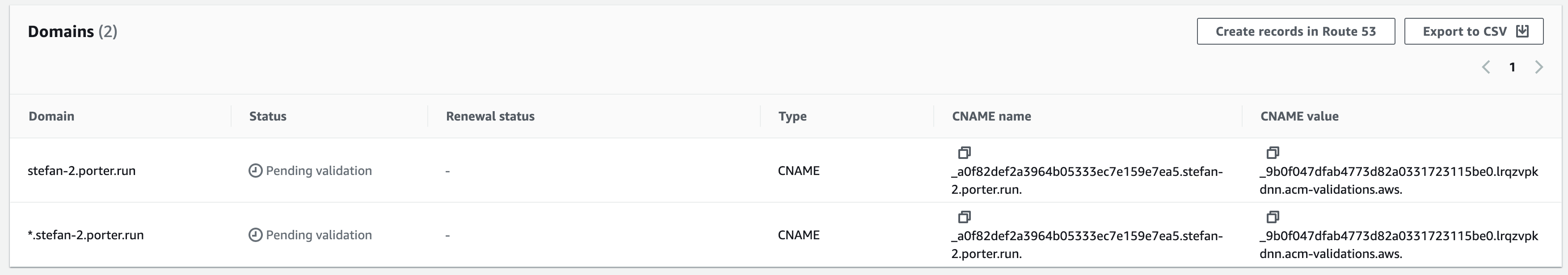
- You may see multiple domains here, all with the same CNAME name and CNAME value. No need to worry about these.
- Go to your DNS provider. This will be CloudFlare in our case.
CloudFlare
-
Select
DNSthenRecords. -
Create a new record - Select
CNAMEfor type.- Enter the value that you pulled from AWS for
CNAME namein theNamefield in CloudFlare. - Enter the value that you pulled from AWS for
CNAME valuein theTargetfield in CloudFlare. - Ensure
Proxy statusis disabled, and is inDNS onlymode. - Set
TTLtoAuto. - Enter
Porter-managed ACM Certificate Verification for YOUR_DOMAINin theCommentfield. This is not required, but is strongly recommended.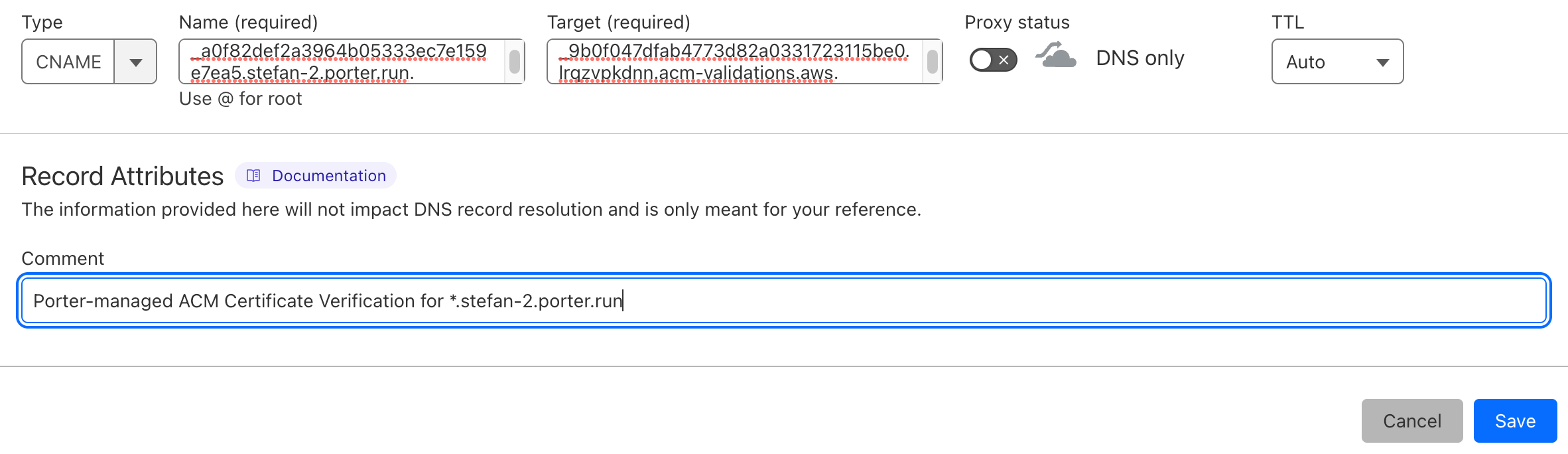
- Enter the value that you pulled from AWS for
- Return to the AWS console.
AWS Certificate Manager - Status
- Go to the ACM Certificate and refresh the page.
- If the status is still
Pending Validation, wait 5 minutes then refresh again. You should now see that the status isIssued.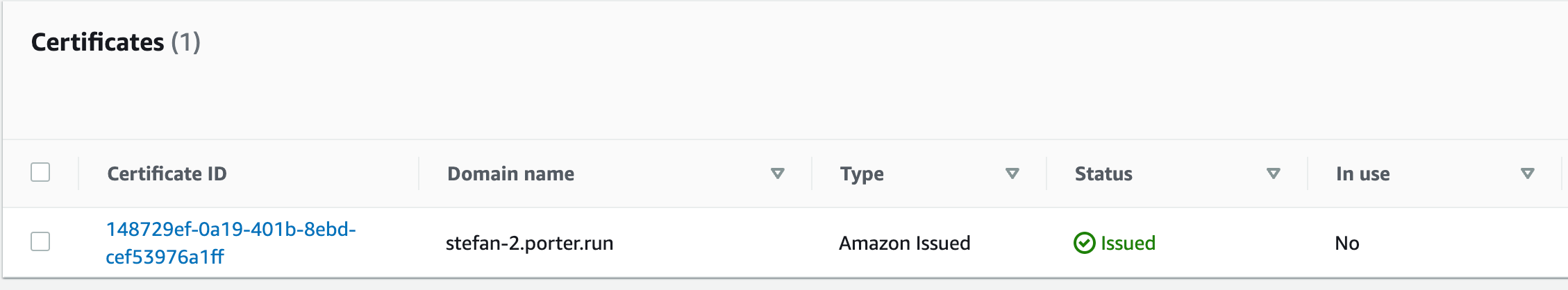
- Your certificate is now issued, and can be used by your ALB.
Creating a CNAME for your wildcard domain
As a reminder, we are usingstefan-2.porter.run as the address that we provided to Porter. All of our protected applications will be available at *.stefan-2.porter.run for example myapp.stefan-2.porter.run or whoami.stefan-2.porter.run.
- Go to your DNS provider. We will be using CloudFlare, but the settings should be similar in any DNS Provider.
1 Select
DNSthenRecords. - Create a new record.
- Select
CNAMEfor type. - Enter the wildcarded domain in the
Namefield i.e.*.stefan-2.porter.run. - Enter the ALB domain name in
Targetfield. This will be provided to you by the Porter engineer. - Ensure
Proxy statusis disabled, and is inDNS onlymode. - Set
TTLtoAuto.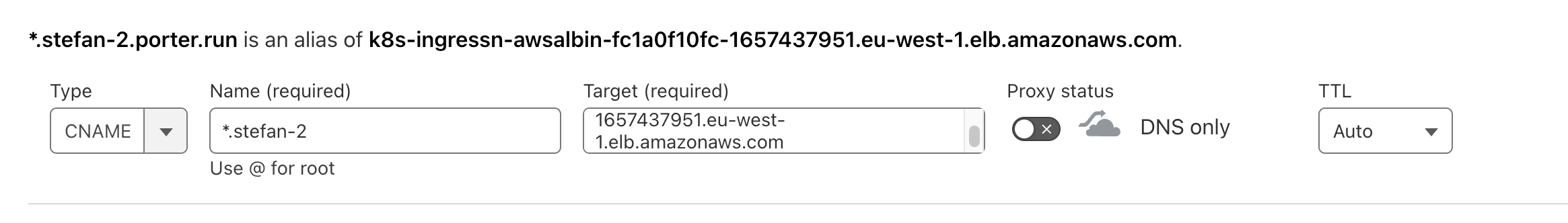
- Select
- You can now use this as a custom domain in Porter for your applications. See Deploying on the Custom Domain to setup your new domain to be compatible with Porter.

