Setting up Tailscale
Creating an Oauth Client
-
In the Tailscale admin dashboard, navigate to
Access controlstab. - Add the following annotations to the policy file:
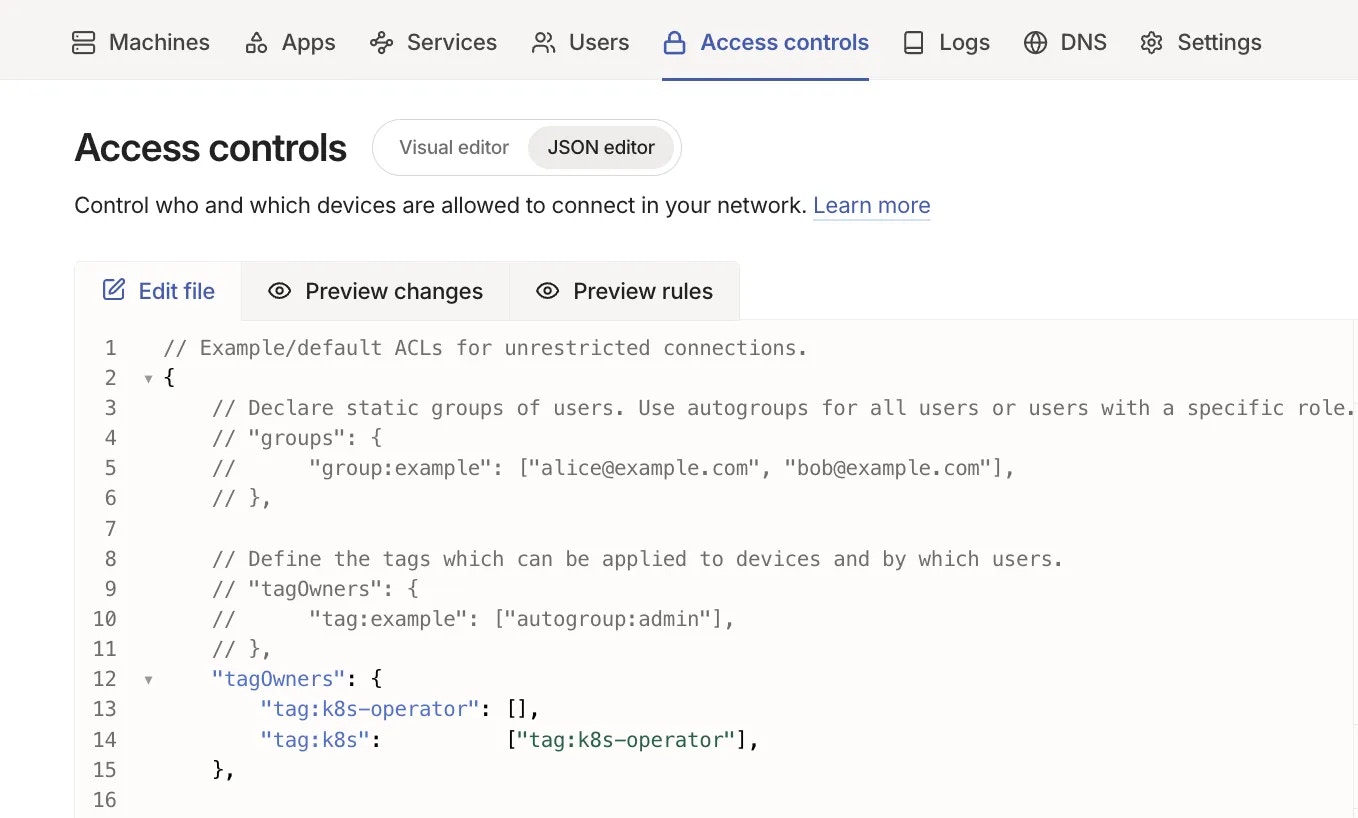
-
Click
Savebutton to save the changes. -
Navigate to
Settings -> Trust credentials -> Add credential -> OAuth -
Select the
CoreandAuth keysscopes with write permissions. Click on “Add tags” and ensure that thek8s-operatortag is selected.
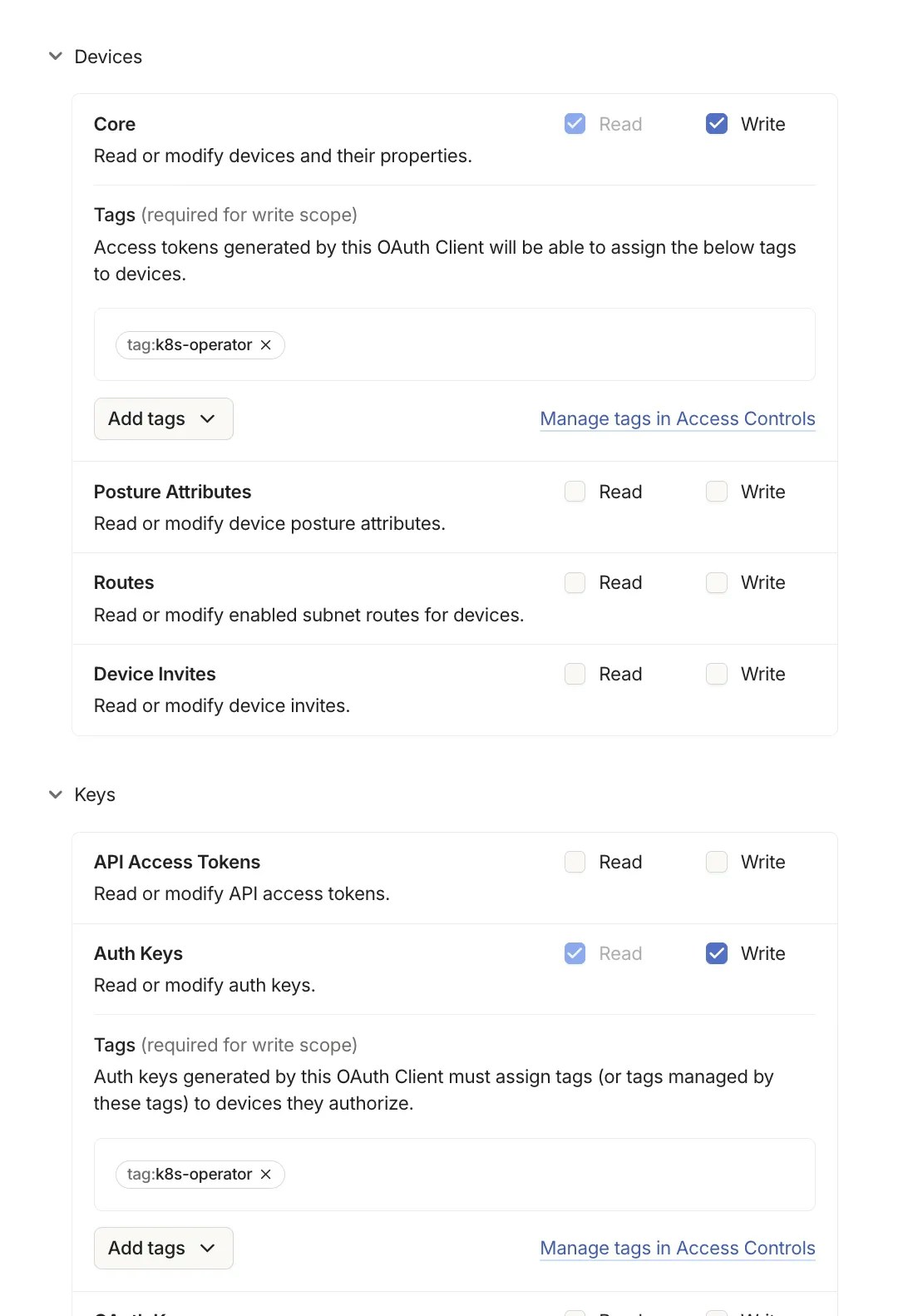
- Click
Generate clientand save the credentials securely - you will need them in the next steps and cannot retrieve them later.
Enabling VPN on your cluster
- On the Porter dashboard, navigate to the cluster where you want to enable Tailscale and go to
Infrastructure -> Cluster -> VPN
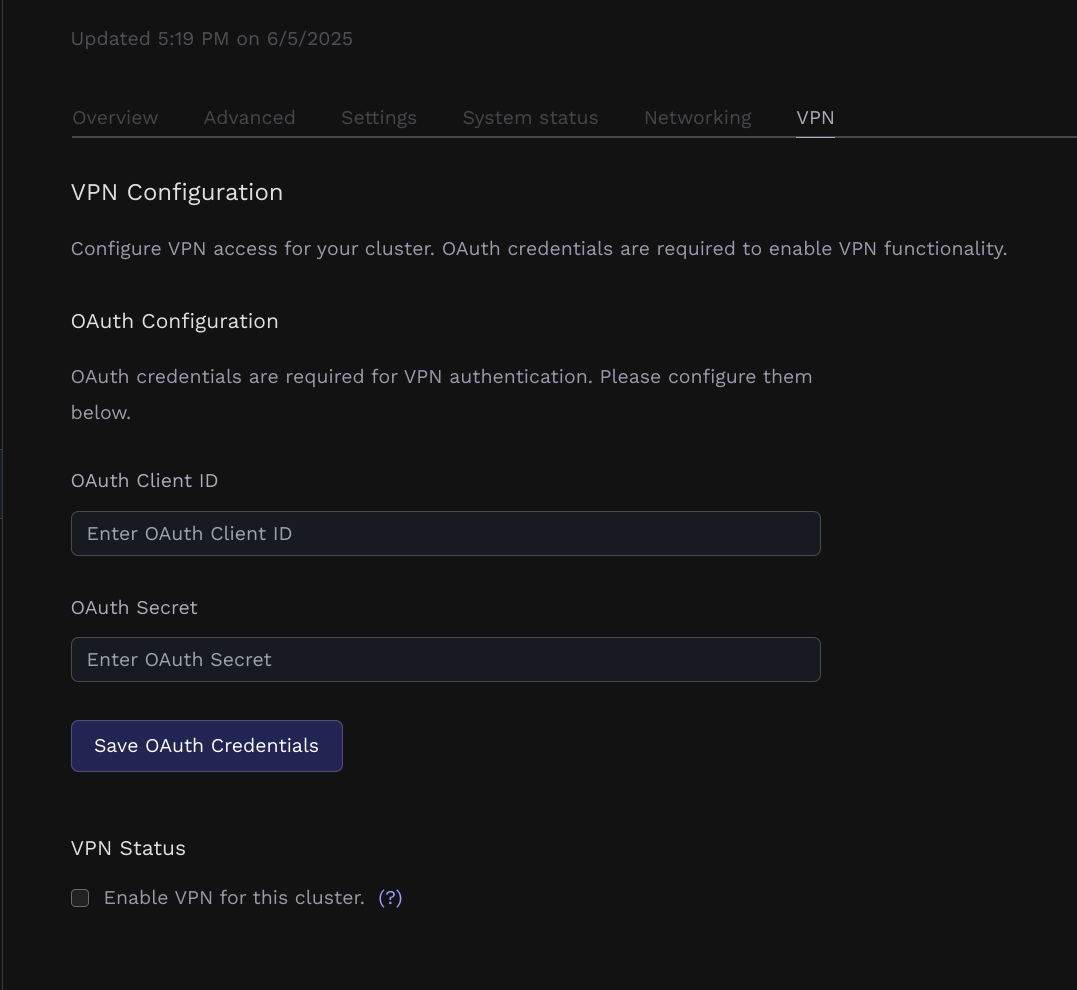
- Input the OAuth client id and secret you generated previously.
- Once the dashboard confirms the credentials are configured, click on “Enable VPN” and update your cluster.
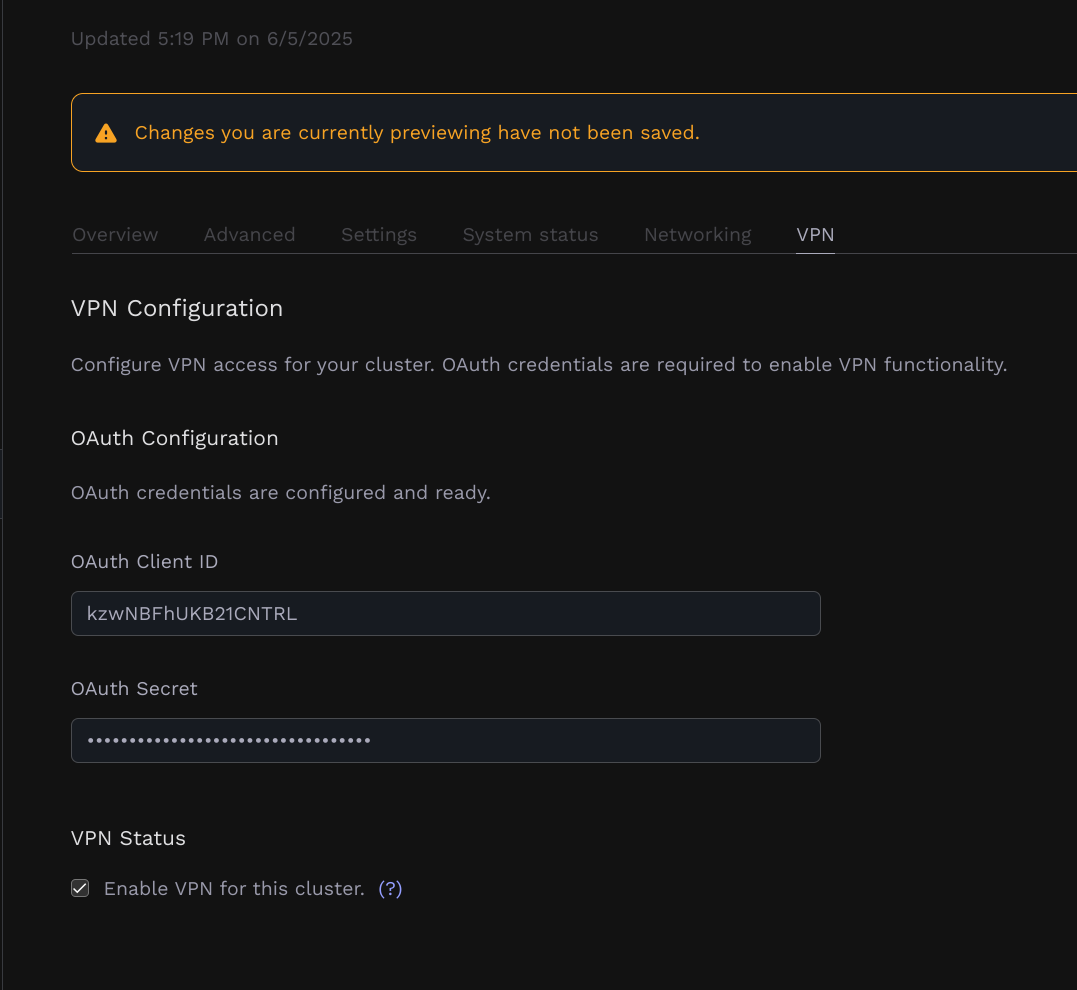
- The cluster will update and once it’s finished, you should be able to see the cluster and tailscale operator in your tailnet.
Adding Routes to your Tailnet
By default, every time that you click “Update” on your cluster from theInfrastructure tab, Porter will ensure that all of your Porter-managed applications and Datastores are accessbile over the Tailnet.
As each route is added, it must be approved by an admin in the Tailscale Admin Panel.
- Visit your Tailscale Admin Panel.
- Click on
Machines. - Find the
cluster-ABCmachine, wherecluster-ABCis the name of the Porter cluster where the VPN integration was enabled. - Click on the 3 dots on the right side of the
cluster-ABC, and clickEdit Route settings - Click
Approve Allto approve all routes. - If you intend to use
porter app runorporter datastore connectcommands, also checkUse as Exit Node.

