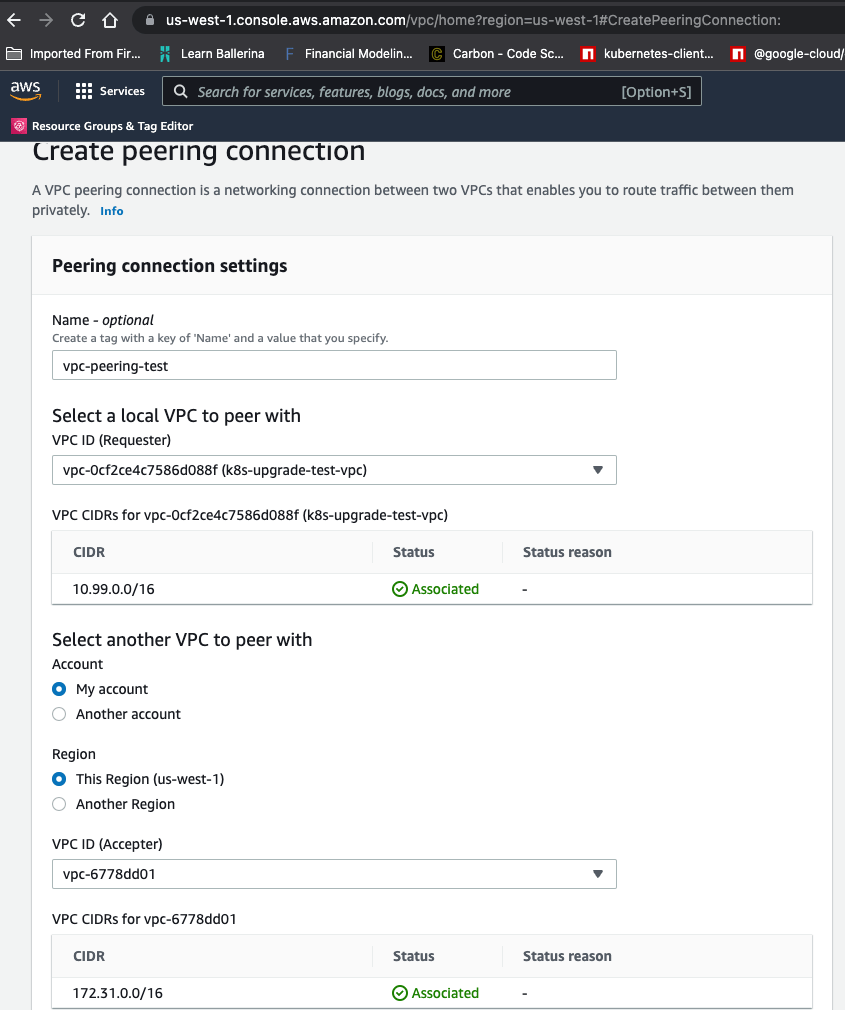
Create a Peering Connection
The first step is to create a peering connection, which can be accomplished by navigating to thePeering Connections section on the VPC dashboard. Whilst creating a connection, note that the requester VPC should be the Porter VPC, and the accepter VPC should be the VPC you wish to create a peering tunnel towards. Note that this is purely for consistency’s sake.
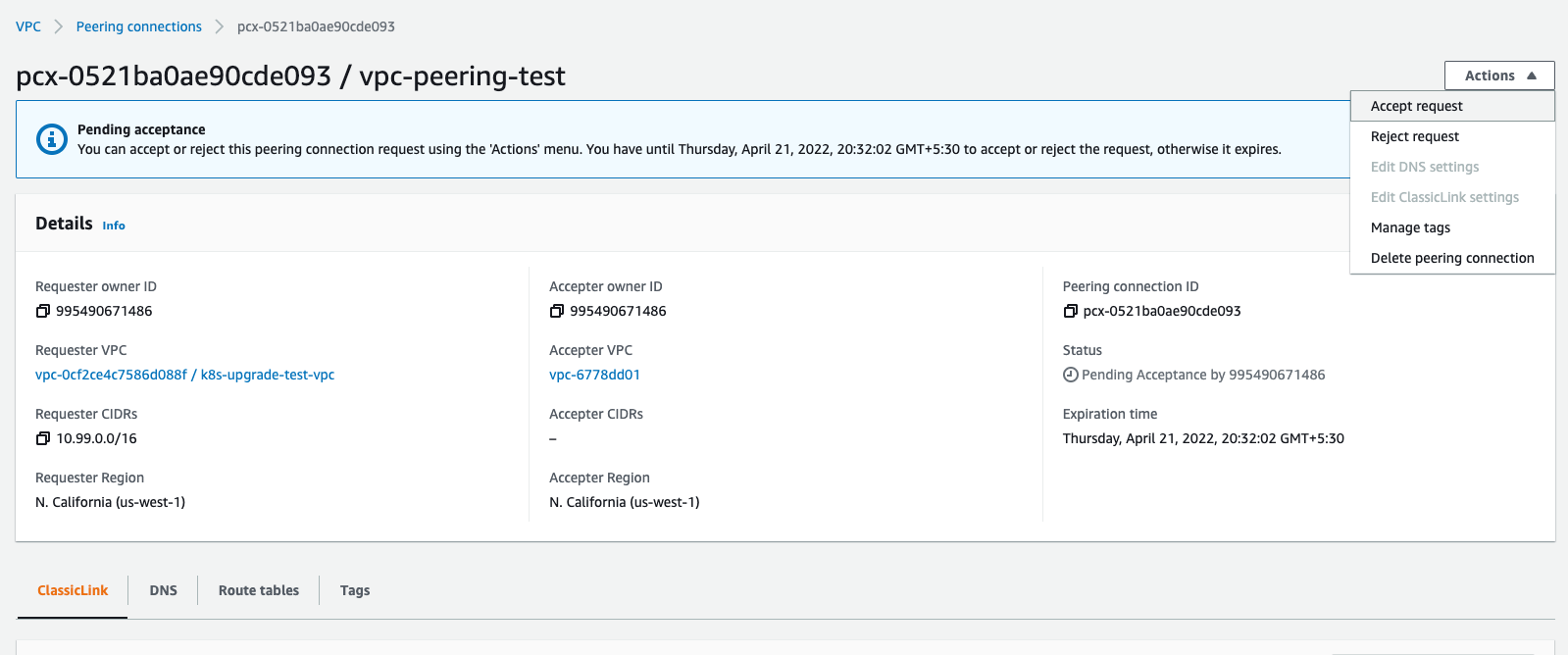
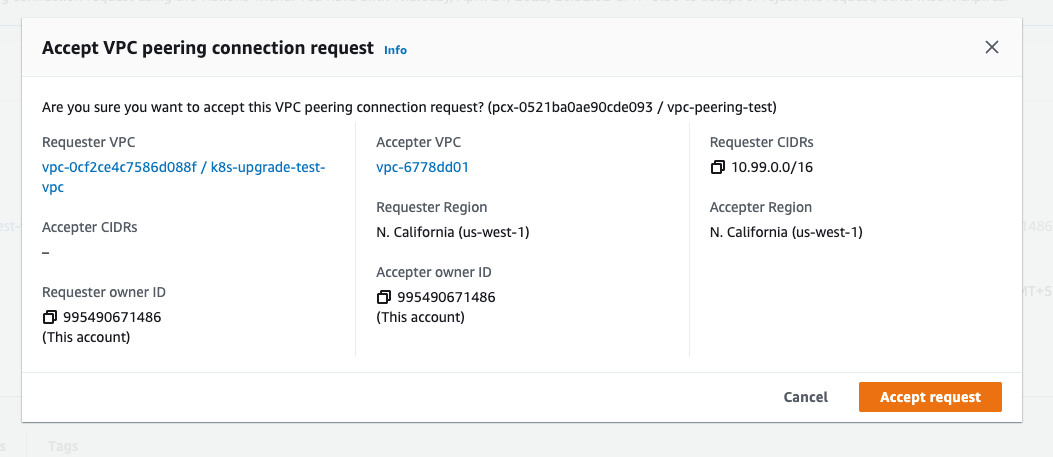
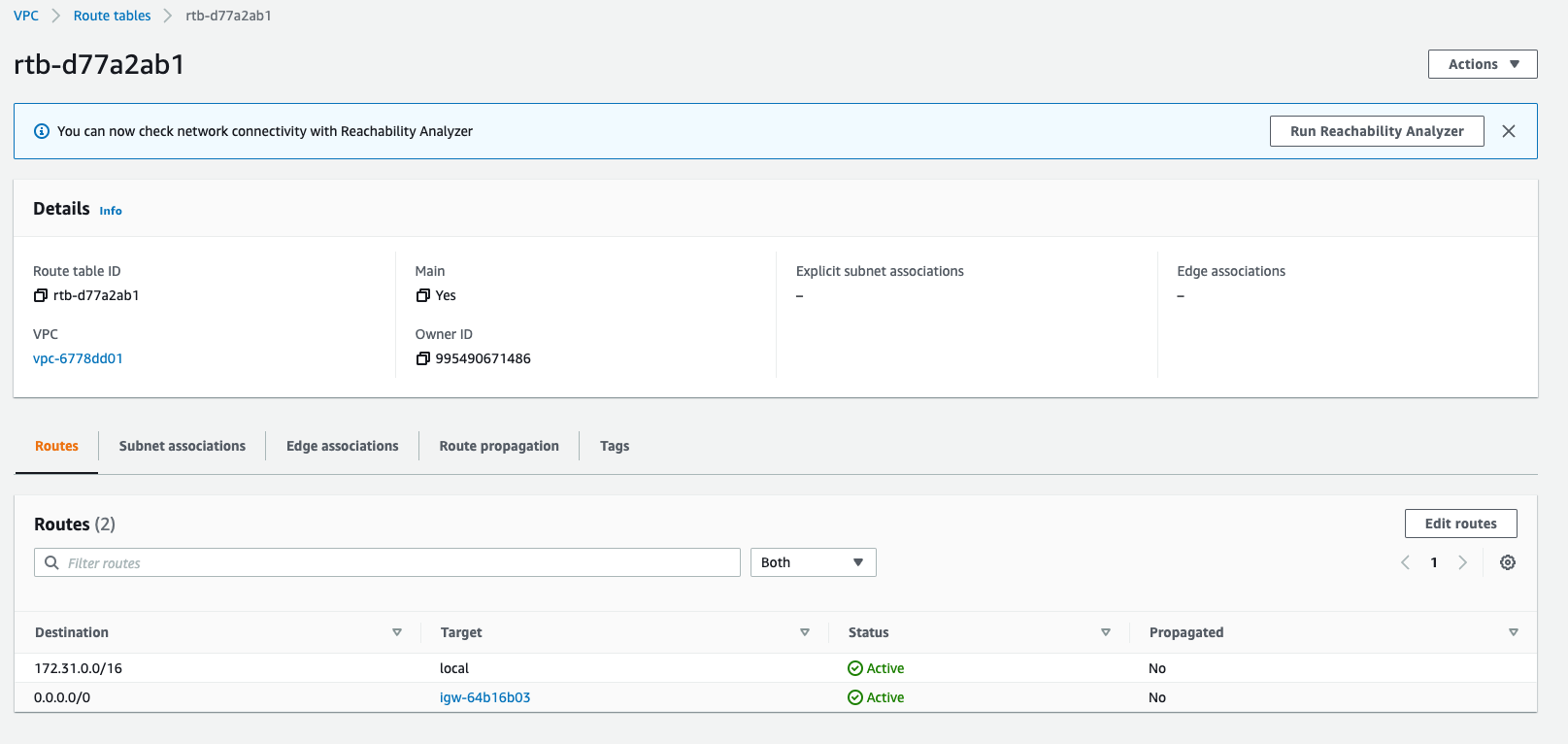
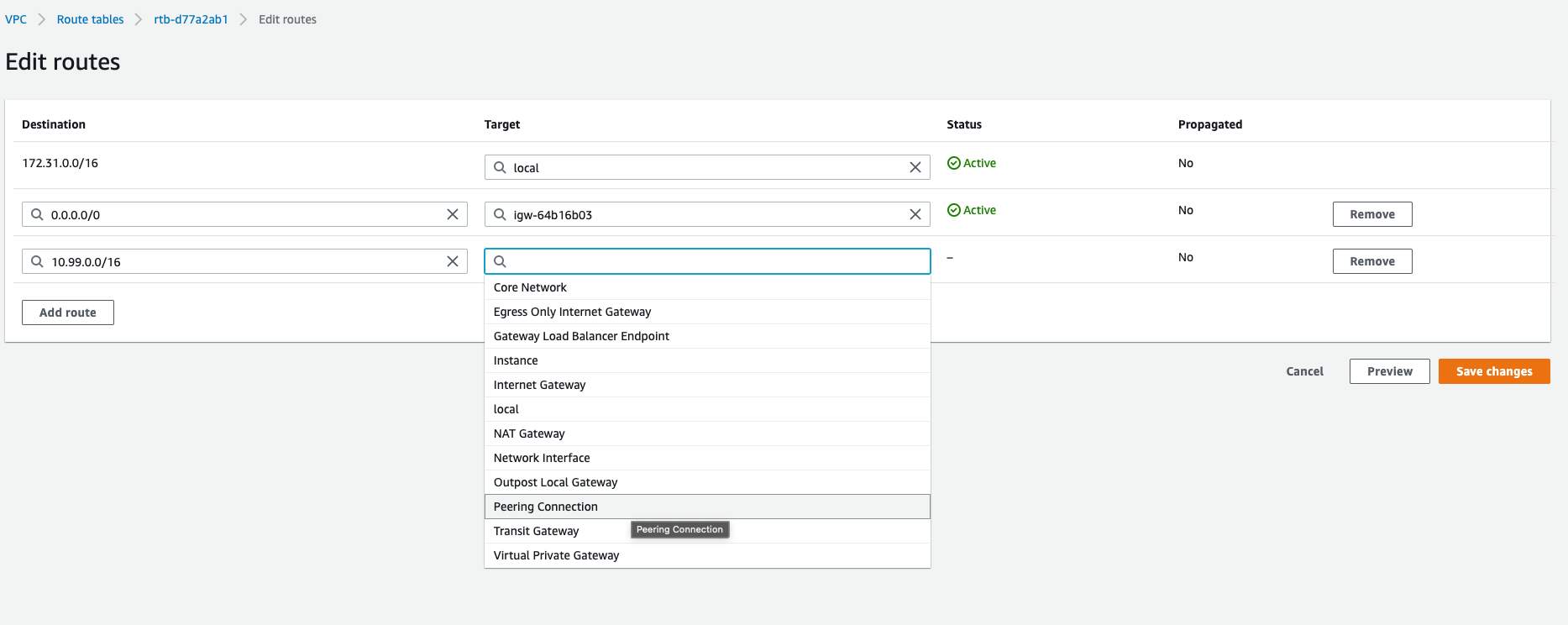
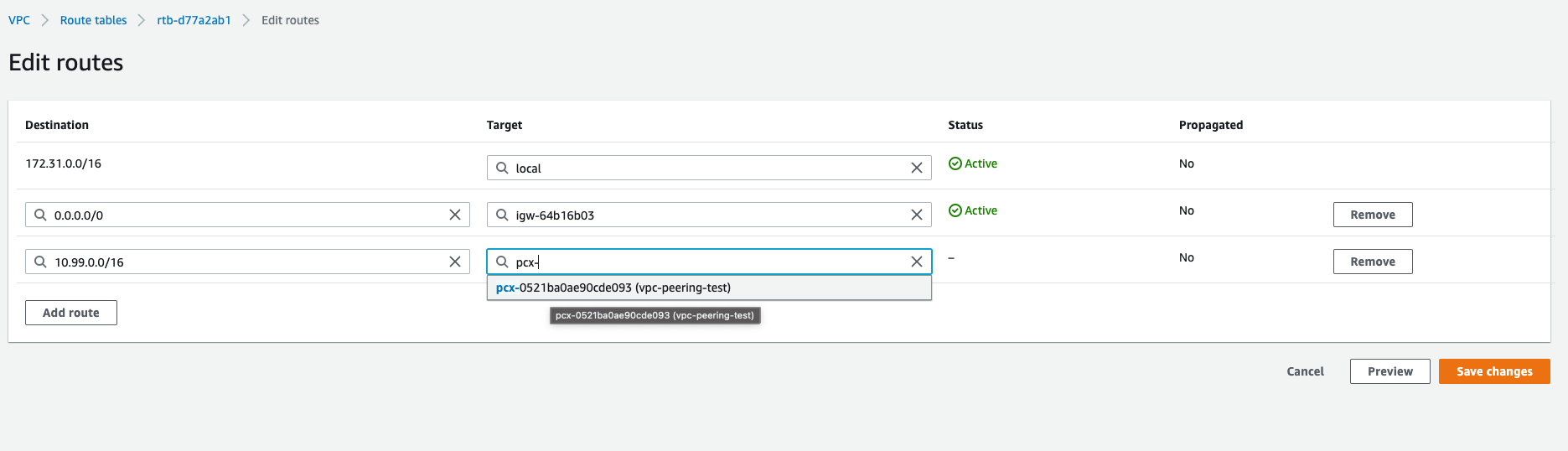
Routing Tables
The next step is to ensure that each VPC’s subnets have routing tables that are updated with entries telling each subnet where to throw traffic for the other VPC’s CIDR. As an example, assume that VPCk8s-upgrade-test-vpc has 10.99.0.0/16 as its CIDR and VPC default has 172.31.0.0/16. In this case, the routing table for each subnet inside k8s-upgrade-test needs to have an entry specifying that traffic for 172.31.0.0/16 is sent to the peering connection, and the routing table for each subnet inside default needs to have an entry that routes traffic for 10.99.0.0/16 to the peering connection.